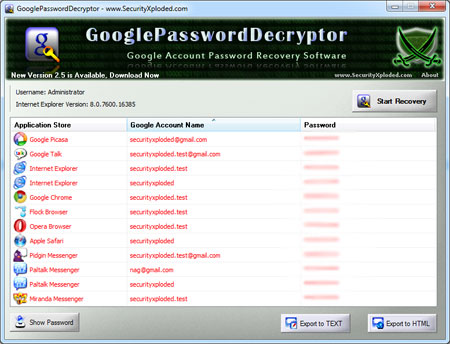
Hey Guys as a Ethical hacker I am always curious to Find the New Loopholes in Existing websites ,softwares and other things... Today over the Internet I found a Very Dangerous Loophole in the Gmail (Best Mailing Services In the World) and I am Going to Share that With You Guys. I have Tried this from my college Network so there Will be Some Assumptions and Tools Needed for that... So Read On...
NOTE: THIS TUTORIAL IS FOR EDUCATIONAL PURPOSES ONLY ! ASSUMPTIONS:1- You are in Local Area Network (LAN) in a switched / wireless environment : example : office , cyber café, Mall etc.
2- You know basic networking information.
Tool used for this attack:1- Cain & Abel or Any Ethernet Capturing Tool
2- Network Miner
3- Firefox web browser with Cookie Editor add-ons (anEC Cookie Editor)
(ALL THE TOOLS MENTIONED HERE ARE AVAILABLE FOR FREE DOWNLOADS YOU JUST HAVE TO GOOGLE THEM)
Attack in detail:We assume you are connected to LAN/Wireless network. Our main goal is to capture Gmail GX cookie from the network. We can only capture cookie when someone is actually using his gmail. I’ve noticed normally in free Classes in College when people normally check their emails. If you are in cyber café or in Mall then there are more chances of catching people using Gmail.
We will go step by step, If you are using Wireless network then you can skip this Step A.
A.) Using Cain to do ARP poisoning and routing:Switch allows unicast traffic mainly to pass through its ports. When X and Y are communicating eachother in switch network then Z will not come to know what X & Y are communicating, so inorder to sniff that communication you would have to poison ARP table of switch for X & Y. In Wireless you don’t have to do poisoning because Wireless Access points act like HUB which forwards any communication to all its ports (recipients).
-> Start Cain from Start > Program > Cain > Cain
-> Click on Start/Stop Snigger tool icon from the tool bar, we will first scan the network to see what all IPs are used in the network and this list will also help us to launch an attack on the victim.
-> Then click on Sniffer Tab then Host Tab below. Right click within that spreadsheet and click on Scan Mac Addresses, from the Target section select
All hosts in my subnet and then press Ok. This will list all host connected in your network. You will notice you won’t see your Physical IP of your machine in that list. How to check your physical IP ?
-> Click on start > Run type cmd and press enter,
-> In the command prompt type Ipconfig and enter. This should show your IP address assign to your PC.
It will have following outputs:
-> Ethernet adapter Local Area Connection:
-> Connection-specific DNS Suffix . : xyz.com
IP Address. . . . . . . . . . . . : 192.168.1.2
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.1
Main thing to know here is your IP address and your Default Gateway.FOR AMU Its : 10.10.50.1
FOR BSNL Its : 192.168.1.1
Make a note of your IP Address & default gateway. From Cain you will see list of IP addresses, here you have to choose any free IP address which is not used anywhere. We assume IP 192.168.1.10 is not used anywhere in the network.
-> Click on Configure > APR > Use Spoof ed IP and MAC Address > IP
Type in 192.168.1.10 and from the poisoning section click on “Use ARP request Packets” and click on OK.
-> Within the Sniffer Tab , below click on APR Tab, from the left hand side click on APR and now click on the right hand top spreadsheet then click on plus sign tool from top. The moment you click that it will show you list of IP address on left hand side. Here we will target the victim IP address and the default gateway.
The purpose is to do ARP poisoning between victim and the default gateway and route the victim traffic via your machine. From the left side click on Victim IP address, we assume victim is using 192.168.1.15. The moment you click on victim IP you will see remaining list on the right hand side here you have to select default gateway IP address i.e. 192.168.1.1 then click on OK.
Finally, Click on Start/Stop Sniffer tool menu once again and next click on Start/Stop APR. This will start poisoning victim and default gateway.
B.) Using Network Miner to capture cookie in plain textWe are using Network miner to capture cookie, but Network miner can be used for manythings from capturing text , image, HTTP parameters, files. Network Miner is normally used in Passive reconnaissance to collect IP, domain and OS finger print of the connected device to your machine. If you don’t have Network miner you can use any other sniffer available like Wireshark, Iris network scanner, NetWitness etc.
We are using This tool because of its ease to use.
-> Open Network Miner by clicking its exe (pls note it requires .Net framework to work).
-> From the “---Select network adaptor in the list---“ click on down arrow and select your adaptor If you are using Ethernet wired network then your adaptor would have Ethernet name and IP address of your machine and if you are using wireless then adaptor name would contain wireless and your IP address. Select the one which you are using and click on start.
Important thing before you start this make sure you are not browsing any websites, or using any Instant Mesaging and you have cleared all cookies from firefox.
-> Click on Credential Tab above. This tab will capture all HTTP cookies , pay a close look on “Host” column you should see somewhere mail.google.com. If you could locate mail.google.com entry then in the same entry right click at Username column and click on “copy username” then open notepad and paste the copied content there.
-> Remove word wrap from notepad and search for GX in the line. Cookie which you have captured will contain many cookies from gmail each would be separated by semicolon ( GX cookie will start with GX= and will end with semicolon you would have to copy everything between = and semicolon
Example : GX= axcvb1mzdwkfefv ; ßcopy only axcvb1mzdwkfefv
Now we have captured GX cookie its time now to use this cookie and replay the attack and log in to victim email id, for this we will use firefox and cookie editor add-ons.
C.) Using Firefox & cookie Editor to replay attack.-> Open Firefox and log in your gmail email account.
-> From firefox click on Tools > cookie Editor.
-> In the filter box type .google.com and Press Filter and from below list search for cookiename GX. If you locate GX then double click on that GX cookie and then from content box delete everything and paste your captured GX cookie from stepB.4 and click on save and then close.
-> From the Address bar of Firefox type mail.google.com and press enter, this should replay victim GX cookie to Gmail server and you would get logged in to victim Gmail email account.
->
Sorry! You can’t change password with cookie attack.(LIMITATION OF ATTACK)SOLUTION: HOW TO PROTECT URSELF FROM THIS HACKGoogle has provided a way out for this attack where you can use secure cookie instead of unsecure cookie. You can enable secure cookie option to always use https from Gmail settings.
Settings > Browser connection > Always use https .
I Hope You Have Enjoyed This ... Any Queries ?? Please Comment










.jpg)